It can be hard to understand amidst all the IT biased (towards Confidentiality, Integrity and Availability of information) cybersecurity hoopla how today’s IT threats emanating from cyberspace can affect industrial control systems. IT security questions can be hard to understand for the ICS practitioner (who leans towards different security priorities of Safety, Availability, Integrity and then Confidentiality) and vice versa. It would be most helpful for both IT and ICS practitioners to see both IT and ICS security concepts demonstrated in the same exercise or simulation.
Two weeks ago I was a guest instructor at the NATO Cooperative Cyber Defence Center of Excellence as part of a CIIP course (https://ccdcoe.org/critical-information-infrastructure-protection-course.html). One of the several highlights for me, which included a visit to a water utility and hearing a lecture about cyber threats from an engineer working for a local power utility, was a demonstration of a cyber-attack directed against the controls of a traffic light system. It was very basic in terms of set up but very impressive. By the way I am sorry if this is a bit sketchy for I am doing this from memory.
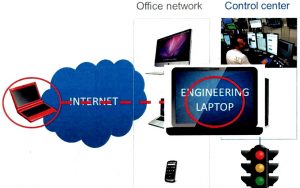
It consisted of a set of Allen-Bradley PLC’s connected to a commonly recognized street traffic light. It was mounted on a portable 3 legged white board stand normally found in most office and small conference rooms. One notebook was connected to the PlC’s which simulated the inside operations of a facility while another notebook was placed a few feet away on a desk which represented an attacker’s computer outside the facility but with some connectivity to the inside. A phishing attack was executed from the outside computer which the victim using the inside computer saw and clicked on. The attacker proceeded to establish a remote foothold on the site by escalating privileges on the victim’s computer and studying documentation about the traffic light control system. The knowledge of the inside of the facility and capabilities gained by the attacker were used to implant malware on the victims computer which found itself on the PLC’s which were used to take over control of the traffic lights. The malware succeeded in neutralizing manual control of the traffic light and later succeeded in putting it into emergency flashing mode. The attacker had complete control of the lights and could do whatever he wanted with the light. I watched this and thought to myself “wow” some of the methods demonstrated by this simulation were probably used in the cyber-attack on the power distribution control systems of Ukraine last year. In summary this kind of portable demo is a relatively inexpensive and labor saving way to demonstrate some key concepts in ICS security for both IT and ICS security practitioners.
Reference:
https://ccdcoe.org/critical-information-infrastructure-protection-course.html
