“The definition of insanity is doing the same thing over and over again and expecting a different result – Attributed to A. Einstein
A recent post titled “Regarding (AA20-049A) Ransomware Impacting Pipeline Operations” on SCADASEC pointed out the FUD promoting aspects of an alert published by The Cybersecurity and Infrastructure Security Agency (CISA) at https://www.us-cert.gov/ncas/alerts/aa20-049a . I fully agree with the points made in this informative post. The main ones being the alerts’ bias toward viewing the security aspects of the network and stopping at the IT/OT levels. The alert loses what little clarity it has when touching on the safety, security and functional questions that lie beyond IT/OT where the ICS/engineering reside. In other words the parts that are closest to actual physical processes relevant to pipeline operations. One example of the alert’s bias and dangerously incomplete understanding of the importance of the physical process of an industrial operation is found in the alerts section on technical details with the subheading “Network and assets”: “The victim failed to implement robust segmentation between the IT and OT networks, which allowed the adversary to traverse the IT-OT boundary and disable assets on both networks.” https://www.us-cert.gov/ncas/alerts/aa20-049a So the area of concern seems focused on keeping what goes on between IT and OT networks in order. What about the devices closest to the physical process going on in the pipeline? The part that is beyond the IT/OT or what many call the ICS side of the operation?
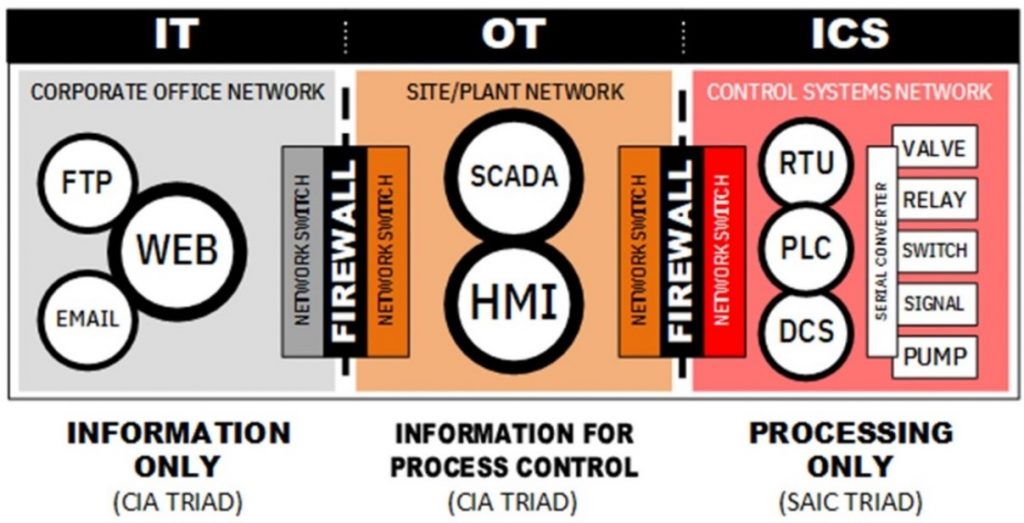
Graphic used with permission of Bob Radvanovsky. http://icsmodel.infracritical.com
The Alert continues this focus with its recommended measures that will ensure the security of IT and OT Networks. For example “Implement and ensure robust Network Segmentation [M1030] between IT and OT networks to limit the ability of adversaries to pivot to the OT network even if the IT network is compromised. Define a demilitarized zone (DMZ) that eliminates unregulated communication between the IT and OT networks.” The use of the word “between” should later followed by and “and ICS” but his does not happen. The focus again and again seems to be IT and OT. If you look at the picture above you will see what is missing which is any mention of the ICS part. The picture below demonstrates that not all the cyber-attacks are limited to the IT and OT parts of an industrial enterprise. ICS is also being targeted for malicious cyber operations.
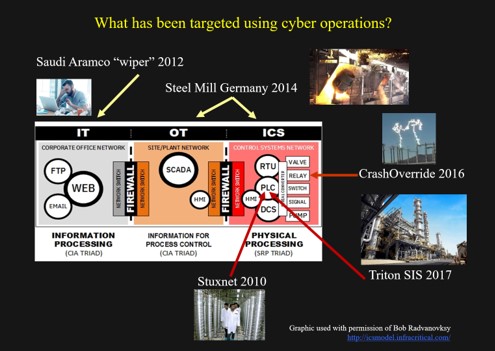
This is probably the most important part that the authors of the alert fail to address. This is worse than just another case of contributing to FUD – it is leading those seeking ways to make their industrial systems safer and more reliable further off the path.
Why is this happening? One explanation can be found in looking at who issued the bulletin. When I looked at the source URL I was confused. Why was it coming from the US-CERT and not the US ICS-CERT? I looked up the website for the ICS-CERT and found it was no longer there. It appears a consolidation that started in 2017 resulted in the former US ICS CERT being merged with the US-CERT under an umbrella organization called “The Cybersecurity and Infrastructure Security Agency (CISA)”. https://www.us-cert.gov/about-us I was most disappointed in this dilution of responsibility for critical infrastructure protection. For years I noted in my presentations to audiences that the world had just a few countries that understood the difference between IT and ICS. For this reason they established dedicated certs for ICS, namely the US and Norway’s Kraft Cert. This alert seems to indicate that the traditional IT biased cert way of thinking (US-CERT mindset) was dominant in preparing this alert. Would the old ICS-CERT have issued such an alert that would be so ignorant of the special technical aspects of ICS?
I am sure that much input is available from the ICS security community of interest to prepare alerts that are more relevant and applicable to ICS. However the stumbling block is the policy making community that seems lacking in understanding of ICS issues and unwilling to listen to those with ICS experience. Alerts that touch on ICS issues should be given to ICS professionals for review and comment prior to their release. This would give one more chance that the alert would be relevant, useful and not contribute to FUD.
Home page (accessed on February 20, 2020) of The Cybersecurity and Infrastructure Security Agency (CISA). For an asset owner, looking for information about ICS security, finding a clear path to knowledge is hard to find. https://www.cisa.gov/
For the US at any rate the policy maker who decided on making infrastructure protection a subheading has taken a step backwards in building critical infrastructure protection capacity.
