Last week I attended two conferences where protection of critical infrastructure were common themes: one focused more on the technical aspects and the other on international security policy. The first was a virtual plenary session of the International Society for Automation (ISA)[1] Committee 99 which is working on updating the standard for Industrial Automation and Control System Security (IACS) ISA 62443. The other was the annual US-Baltic Quadrilateral Consultations on Cybersecurity and Infrastructure Protection attended by representatives of the US DOS, US DHS, and the national institutions responsible for cybersecurity in Lithuania, Latvia and Lithuania. In addition representatives from each Baltic country’s MoD and MFA participated and lead off the discussions. In the former I was a passive participant and in the latter I was one of the presenters and would like to share my take-a ways from these different meetings with a focus on how we are protecting the critical infrastructure fundamental to modern economic activity, national security and well-being of society.
The ISA plenary was a true World Class Act. Reports from 10 dedicated workgroups on a wide range of IACS issues including IoT, case studies and outreach efforts[2] were most impressive. The ISA 62443 provides a toolbox produced by engineers for use by both engineers and management to cover the entire IACS life-cycle. However, there was just one concern. As someone with a defense and security background I missed an appreciation for the threat landscape which seemed to be absent from the deliberations. I have written before about the importance of answering the 3 Questions when constructing security policies[3]. It may be that these threats have long been assumed or there was no time during a short session to go into them. This lack of appreciation of threats did not bother me that much until I attended the second virtual US-BALTIC consultations on cyber security. A potentially important conference for its implications but only briefly mentioned in public[4].
The US-Baltic virtual conference was somewhat chaotic compared to ISA’s plenary session. In an event planned for 3 hours with speakers limited to 3-4 minutes each the schedule was an hour late before the middle of the program was encountered. The participants were mostly diplomats working for their respective DoS/MFA’s or civil servants working for an MoD or CERT. In waiting in line my time to speak someone scheduled after me asked to present their slides “right now”. The moderator agreed to this change in an already late schedule and the expression “shepherd herding cats” came to mind.
These were just organizational annoyances that I have experienced before while attending such conferences for 27 years. However, what really caught my attention was the stress on the cybercrime threat to citizens, financial institutions and on the coming elections (Lithuania held its Parliamentary (SEIMAS) election recently). I asked myself “what about the threats to the utilities and technologies that provide the electricity, fuel, heat and water? How would those elections have fared if there was a power blackout on Election Day?
To the great credit of the US delegation they did make a point of mentioning malicious cyber activities of states on critical infrastructure and included terms such as ICS to describe them. Using the chat feature I thanked them for pointing out that we were not just concerned with Office IT but were also concerned about preserving the well-being of OT/ICS used to monitor and control a physical industrial process. (to my pleasant surprise the US delegation even had someone who replied and identified himself as an industrial engineer).
However the overwhelming emphasis from my 3 Baltic colleagues was on the cybercrime threat stressed by the 3 National CERTs represented in the meeting. As each Baltic nation made its report I heard much surprise from the other in terms of the incidents being reported “we never knew this happened in your country”. I put out a question in the chat: “what happened to the 3 Baltic MoU signed by the 3 responsible cybersecurity institutions in 2015? The MoU contained agreed upon mechanisms for sharing information and other forms of cooperating in defending against cyber threats. There was even language to cover critical infrastructure in addition to defending Office IT. No one commented back on why this MoU, signed with 3 recognized national electronic signatures with much fanfare[5] a few years back was missing in our dialogue.

One more disturbing element in the meeting was the delight expressed by one country’s representative on its moving from 53rd place to the top 10 in national ratings for cybersecurity. One of the reasons for this improvement was the progress made in modernizing the security footing of the energy and other sectors of Critical Information Infrastructure (italics mine). I could see no evidence presented as to what this meant beyond the language of cybercrime, DDOS and other threats to Office IT. Not much convincing semantics having to do with OT/ICS protection in the utility and industrial sectors. Worst of all I could got no sense that the participants coming from diplomatic non-engineering backgrounds had any clue as to what control systems were for and where they were in terms of the physical process of generating and distributing electricity, pumping or compressing fuel down a pipeline, running trains on tracks or distributing drinking water to homes.
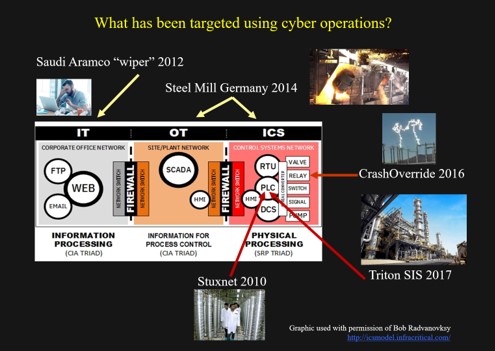
International norms (Confidence and Security Building Measures or CSBMs/CBM’s) for states to follow in cyberspace were discussed and in my opinion there was some self-satisfaction in the progress made by their national representatives’ work on this topic in the UN, OSCE, EU and other international security organizations. When it came to make my presentation on the theme of international cybersecurity agenda I felt my hand moving toward the “hornets nest” in mentioning that I co-chaired (with the US) the first meeting on CSBM at the OSCE in Vienna in 2012[6]. I said that since then, IMHO, very little concrete progress has been achieved. Malicious state actors have seen since the time of Stuxnet (2010) have come to learn that directing malicious cyber activity at the critical infrastructure of other states continues to be effective, cheap and deniable. This dangerous activity, alas, is becoming acceptable as a Norm. As one industry opinion leader recently wrote a de facto norm is already being followed: “It is expected and known an adversary will attempt to gain a foothold in critical infrastructure ICS, perform reconnaissance, and prepare to perform an attack to disable the underlying process.”[7]

I then put my hand into the “hornets nest” when I gave a low rating to 10 years of the “accomplishments” by the international security policy making community in reducing risks to national critical infrastructure from state or state supported Advanced Persistent Threats. Their failure in arriving at concrete norms to restrain states from this destabilizing behavior for our common cyberspace security environments has placed an unfair burden on engineers working in sectors of critical infrastructure such as energy, water and transportation. To add to their daily efforts in keeping their industrial and engineering operations up and running so all who flip a switch will get light and those who open a tap, clean water, engineers now must deal with defending against state resourced and executed attacks. This I said was an unfair burden for plant engineers and their colleagues. In soccer this would be the equivalent of pushing a High School team into a match with a FIFA cup champion. In this situation one can expect no mercy from the cyber 007’s and the outcome of the match would be a foregone conclusion. The message for the engineers is that you are on your own and do not expect any help from the security policy community to do anything to raise the bar for playing games with their critical systems. I guess in this diplomatic gathering my intervention earned me the title of “Mr. Cybersecurity Persona non Grata”
This is sounding too pessimistic. Perhaps there can be a positive outcome to this Tale of the Two Conferences? It would make me fell much better if the participants at both conferences were made aware of what each was doing and started to invite each other to their next conference. Invite a representative from the engineering conference to say a few words to the other diplomatic conference and vice versa. Maybe this is worth a try? What do you think?

.
[1] https://www.linkedin.com/company/isa/ https://www.isa.org/
[2] The ISA had just published its Quick Guide to 62443. See https://gca.isa.org/isagca-quick-start-guide-62443-standards
[3] See http://scadamag.infracritical.com/index.php/2018/02/21/towards-cyber-safe-critical-infrastructure-answering-3-questions/
[4] Other than a brief neutral Twitter tweet from one of the participants, no information about this conference either from the host or any other national sites I visited at the time of this writing.
[5] See Butrimas, V., “Baltic Cyber Cooperation” https://perconcordiam.com/perCon_V7N2_ENG.pdf p.18
[6] Some information about these first consultations and exchanges of view on CBM’s has leaked out. See Carr, J., OSCE’s CBM’s revealed by anonymous., Digital Dao, November 13, 2012. https://jeffreycarr.blogspot.com/2012/11/osces-cyber-security-confidence.html Accessed October 16, 2020.
[7] Pederson, D., Cyber Conflict Norms in ICS, September 20, 2020 https://www.linkedin.com/pulse/cyber-conflict-norms-ics-dale-peterson/ accessed October 16, 2020
