“But as soon as we find out that it’s state-sponsored, or there may be state actors involved, we back away from that.” – Interpol digital crime centre director Sanjay Virmani
Seems that the WannaCry incident should appear on anyone’s short list of notable cyber incidents of 2017 (so far). Some reports in the press have referred to this as a “wake-up call” (1). Since Stuxnet in 2010 there have been other such wake up calls but it seems many remain in deep sleep and instead of an alarm a good shove and yell in the ear of the sleeper may be in order. In terms of WannaCry and the cybercrime threat reaching industrial control systems, I found two articles written before May 12 that predicted this would happen. One article which was published in December 2016 has recently been republished.(2) Another report comes from a recent ICS conference in Singapore.(3)
From the other reports I have read about WannaCry since May 12 and judging from the published screen shots the infections were limited to the office side IT and did not make it to the OT side. Public screens displaying train schedules were disrupted but no trains were caused to derail.
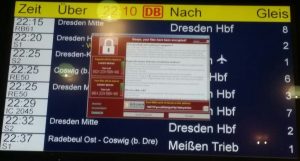
Enough FUD apparently was generated to cause some manufacturers and operators to shut down or reduce their operations out of caution (4). Thought that the control system world could go on without having to worry about attacks from cyber criminals but things have changed. Now what can be done about it? If cyber criminals start switching their targets from hospitals to manufacturing and sectors of critical infrastructure then we can refer to law enforcement and international cooperation (there is the European Council Convention on Cybercrime and other legal instruments to apply) to catch and prosecute the perpetrators.
A new problem appears however. What to do if states backed up with their impressive resources decide to engage in this malicious activity? If one can believe the reports that, the warhead part of WannCry came from the cyber arsenal of a state then this idea is not far-fetched. Calling this state activity a cybercrime and going after the perpetrators using law enforcement may not work out very well. I have a quote somewhere from the director of Interpol who stated that if the cybercrime investigation leads to evidence of state involvement they drop the case (5). Wake up calls have been ringing for both the hi-tech engineering and international security policy communities for some time. Both need to get together and start discussing ways to manage this before the next “wake-up-call” happens.
Proposals for norms of state behavior in cyberspace have been on the table for some time (6). They need to be taken up and seriously considered now. Perhaps this will also generate enough support for self-restraint and for more aggressive international cooperation to keep cybercriminals from thinking placing ransomware on a control system is worth the risk.
References:
1 Microsoft warns ransomware cyber-attack is a wake-up call
15 May 2017 http://www.bbc.com/news/technology-39915440
2 Ready for Ransomware? (originally published in December 2016)
May 16, 2017 by Sean Lyngaas – Contributing editor
* http://advancedmanufacturing.org/ready-for-ransomware/?utm_source=twitter&utm_medium=social&utm_campaign=SocialWarfare *
3 New SCADA Flaws Allow Ransomware Other Attacks
http://www.securityweek.com/new-scada-flaws-allow-ransomware-other-attacks
By Eduard Kovacs on April 27, 2017
4 Ransomware and control system cyber security
Submitted by Joe Weiss on Tue, 05/16/2017 – 00:42
http://www.controlglobal.com/blogs/unfettered/ransomware-and-control-system-cyber-security/
5 Inside Interpols digital crime centre
http://www.itnews.com.au/news/inside-interpols-digital-crime-centre-410768?eid=3&edate=20151021&utm_source=20151021_PM&utm_medium=newsletter&utm_campaign=daily_newsletter
By Andrew Sadauskas on Oct 21, 2015 11:00AM
6 For the latest see: “Microsoft Outlines Cyber Geneva Convention Proposal”, Marks, J., April 24, 2017. http://www.nextgov.com/cybersecurity/2017/04/microsoft-outlines-cyber-geneva-convention-proposal/137043/?oref=nextgov_today_nl
