The year is ending and there have been several unsettling events in cyberspace this past year to reflect upon. They all seemed to have come together for me this past week as I completed my speaking engagements in Vilnius and in Garmische-Partenkirchen. The first conference was in Vilnius with the title “Baltic Energy Summit 2017 ”. The two main organizers were legal firms from the U.K. and from Finland. (1) I have been to these kinds of conferences before. The theme of energy security is usually discussed within the framework of having a reliable energy source ,“security of supply” and a steady price “security of price”. In addition, the legal, regulatory and market challenges of the energy sector are explored and discussed. I usually wait for a while before raising my hand to point out that both supply and price depend on an additional security factor, “security of technology”. I argue that if the technology used to pump fuel down a pipeline fails or causes a power plant to shut down there will also be an effect on the security of supply and price. The point made is that there is a third security concern that is being missed and should be considered at this conference (really hard to stand up like a third thumb and say this sometimes but I am getting used to it).
At this conference, I refrained from raising my hand the first day since I knew that I will have a chance to speak on the second day as a member of a panel session on cybersecurity and energy. I patiently waited and was able to make my point about the need to address the “Cybersecurity dimension of Critical Energy Infrastructure”. The points were very well taken indeed and people came by afterwards to exchange business cards and mention about the conference they are planning to attend. One of them was about renewable energy, which will feature wind power. I was amused as I sometimes feel like a cyber security “Don Quixote”. Just imagine a cyber DQ is invited to speak at a windmill conference about cyber issues. Seriously, this was an excellent conference. I learned as much from it in terms of improving my knowledge of a regional energy market as I gave to it.
The second conference was at an educational institution on international security run by US and German defense institutions. Have been a frequent guest over the years and yes they again asked that I make my “Cybersecurity dimension of Critical Energy Infrastructure” lecture as part of a two-week course on cybersecurity. I looked forward to it as my second last trip of the year to a beautiful mountain valley setting in Bavaria. Participants came from governments, militaries, law enforcement and private sector from countries in Europe, Africa, North and South America and Asia. Just as in the other conference I listened to all the talk and waited for my time to speak where I would again point out that it is not enough to think about cybersecurity in terms of cybercrime, socially motivated hackers, and cyber spying states. However in the morning session before my lecture later that day there was a panel devoted to Internet freedom and International Law. I was tempted to react to one of the speakers whose presentation was titled “A Duty to Hack”. (2)
The speaker was a law professor coming from well-known legal faculty of a university. The main thesis or proposal sounded like a variation of “if you can’t beat them, join them” argument. However the proposal potentially had serious implications in terms of the growing challenge of managing the malicious cyber activities of APT’s operating in cyberspace today. It was unsettling to hear of a proposal justifying and perhaps giving legal cover for the proliferation of state sponsored cyber attacks on critical infrastructure.
The proposal went like this –
“The Duty to Hack would require States to use cyber-operations in their military operations whenever they are the least harmful means available for achieving military objectives. Thus, if a State can achieve the same military objective by bombing a factory or using a cyber-operation to take it off-line temporarily, the Duty to Hack requires that State to pursue the latter course.”
I was shocked to hear this coming from a representative of the legal community. Someone who represents a sphere of activity associated with a respect for and rule of law. In short a proponent of civilized behavior. Not much progress toward promoting civilized behavior in cyberspace was made in the international arena during the past year. Especially when earlier this year the United Nations Government Group of Experts failed to agree on norms or standards of conduct for states to follow in cyberspace (3). 2017 was not a good year for making cyberspace and critical infrastructure safer. If anything things were going downhill fast if proposals like this are being given legitimacy in international fora. This proposal was made public earlier in the Spring of 2014 (about a 100 yrs. after the start of World War I) in a published paper Very strange to hear this proposal at a conference in 2017 after the Federal IT Department of the German Government published its cyber report of a cyber intrusion and uncontrolled emergency shutdown at a steel plant in the Fall of 2014 and after the first cyber-attack in December 2015 on the controls systems of an operator of a regional power grid in Ukraine. Not to mention all the reports about the Shadow Brokers, Wanna Cry, NotPetya and all other incidents in between. Clearly, this law professor was not “getting it” either through being poorly informed about what has been going on in cyberspace these past years or through a lack of imagination. Something that could perhaps been remedied by having some contact with a control system engineer working in critical infrastructure.
The engineer perhaps could have explained to the lawyer that using a cyber weapon to disable the cooling system of a nuclear reactor instead of a precision guided bomb for the sake of avoiding collateral damage may still result in a reactor melt down. You cannot be so sure about the effects of a cyber attack on a real time critical system. Mention was made during the presentation about the effects of STUXNET. That it was found in India and other parts of the world and nothing happened. Perhaps this was being presented as a support for the level of precision that can be achieved with a cyber weapon as opposed to bombing? If so there is a flaw in this reasoning as it is supported by a lack of understanding about the way STUXNET worked. STUXNET was designed with such precision in mind but it still did unexpected things. Part of the malware was programmed to first confirm where it was according to some specifically listed criteria ( had to be in a nuclear enrichment facility using this kind of cascading system of centrifuges and using Siemens PLC’s. and so forth). If the location did not meet the criteria then the malware deactivated itself. However some say something went wrong in that it found its way to the Internet where it spread and where the code could be captured, shared and analyzed. This may have been a close call. Just consider if there was a mistake in the code and the malware proceeded to disrupt the control systems in places it was not supposed to be?

.

.
Playing cyber games with a control system remotely monitoring and controlling a real-time critical physical process can have consequences that are hard to predict. Can one say with enough certainty that the effects of a cyber attack will different from a kinetic attack. Look at the Fukushima nuclear disaster where safety systems and sensor data were lost because of a power failure caused by a tsunami and the aftermath of the DC Metro collision caused by the failure of one sensor. The pictures both look like the aftereffects of a military bombing. If one did not recognize the photographs could one really tell which one was caused by a cyber event? It is unsettling to think that the cyber option for attacking another states critical infrastructure will limit collateral damage more effectively than when using a precision bomb.

.
.

The proposal is also seriously flawed in the sense that supporting a “duty to hack” can only contribute to the further destabilizing of the international security order. The international laws for war and for protecting human rights of civilians may still be applicable. There is a significant fault in the argument however. While a military strike with a traditional bomb is visible in terms of cause (who did it) and effect it does not apply if this was a military strike with a cyber weapon. In the former, we know who did it while in the latter we are not likely to know. In the former there is a possibility of arriving at some justice that will lead to future restraint in terms of dealing with the effects of public opinion and the “CNN effect” but in the latter the act is likely to be repeated and with some encouragement. In other words, things may get out of hand quickly. Especially if the victim state makes a mistake in picking the wrong country for retaliation.
In my presentations about cyber and threats to critical infrastructure, I make a point of raising awareness. I use several examples to illustrate. I describe the implications of the Olympic Pipeline Explosion, German steel mill attack and the cyber-attacks on Ukraine’s industrial control systems and others as time allows. It seems to work but I am worried about one thing. Something is missing. Especially when one is in a room full of lawyers and diplomats discussing cyber misbehavior of states. Do the engineers need a voice in these discussions of international law and cybersecurity policies? I think so and would encourage the engineering community to make their voices heard in these debates. A way must be found to get the attention of the authors of these proposals and explain in layman’s terms the implications of what they are proposing.
Perhaps a letter signed by a representative group of SCADASEC could be arranged and sent when and to where it is needed? Recently some opinion leaders of the Internet signed and sent an open letter (4) to government officials over the proposed changes to the Net Neutrality regulations. Perhaps this model can be used?
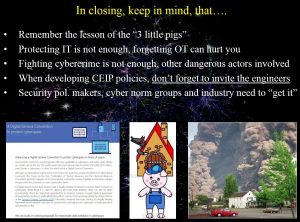
Here is a copy of my summary slide that I show towards the close of my presentations and the main points covered. Please note the importance of including the engineers. Perhaps I should raise it to the top of the list?
• Remember the lesson of the “3 little pigs”, only one got it right
• Protecting IT is not enough, forgetting OT can hurt you
• Fighting cybercrime is not enough, other dangerous actors involved
• When developing CEIP policies, don’t forget to invite the engineers
• Security policy makers, cyber norm groups and industry need to “get it”
As Klaatu said at the end of the 1951 film, “The Day the Earth Stood Still” … ”the decision, rests with you [us]” (5)
Vilnius, December 11, 2017
References:
1. Baltic Energy Summit 2017 Program. http://www.eelevents.co.uk/upcoming-events/baltic-energy-summit-2017 (was a late invite to the conference so I am not listed in the on-line version of the program)
2. Duncan B. Hollis, Re-Thinking the Boundaries of Law in Cyberspace: A Duty to Hack? Cyberwar: Law & Ethics for Virtual Conflicts (J. Ohlin et al., eds., Oxford University Press, 2014 Forthcoming)Temple University Legal Studies Research Paper No. 2014-1653 Pages, Posted: 14 Apr 2014. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2424230#%23
3. S. Soesanto and F. D’Incau, The UN GGE is dead: Time to fall forward, http://www.ecfr.eu/article/commentary_time_to_fall_forward_on_cyber_governance 15th August 2017
4. Internet Pioneers and Leaders Tell the FCC: You Don’t Understand How the Internet Works https://pioneersfornetneutrality.tumblr.com/
5. Nice film where you can see electrical infrastructure neutralized. In the film an alien visitor used his civilizations’ technology to perform this feat. Today’s earth technology now has this capability. Just remember “Gort” may be out there.

